![]()
The first role-specific labs I'll be documenting will come from TryHackMe's SOC Level 1 learning path & certificate!
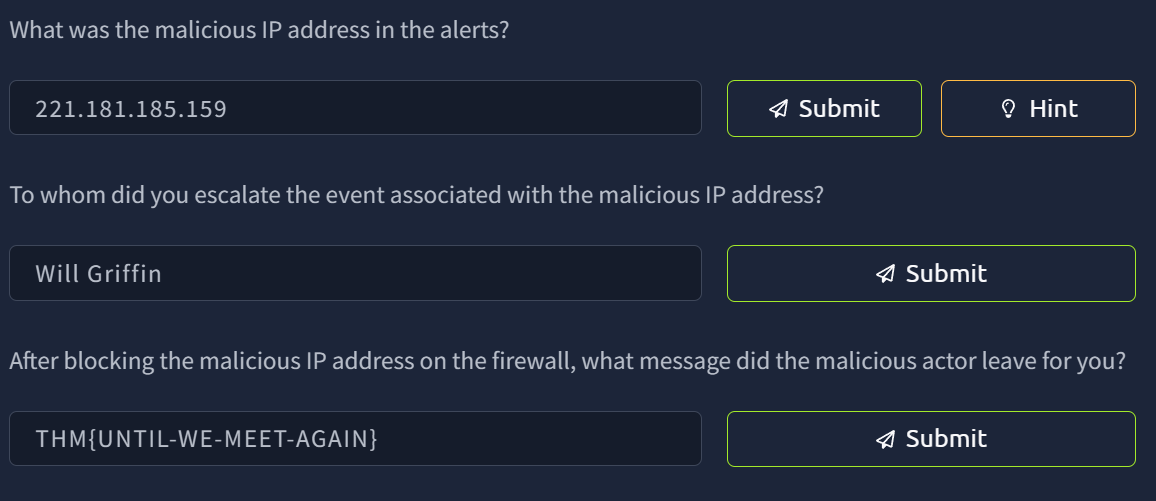
Right off the bat and from the very first module, they have us using a simplified, mock SIEM to identify a malicious connection attempt, use a mock open-source IP address database to determine if the IP is known to be malicious, escalate the alert to the correct team member (in this case, the SOC Team Lead) and then block the IP address in the firewall once given permission to do so.
See photos below:
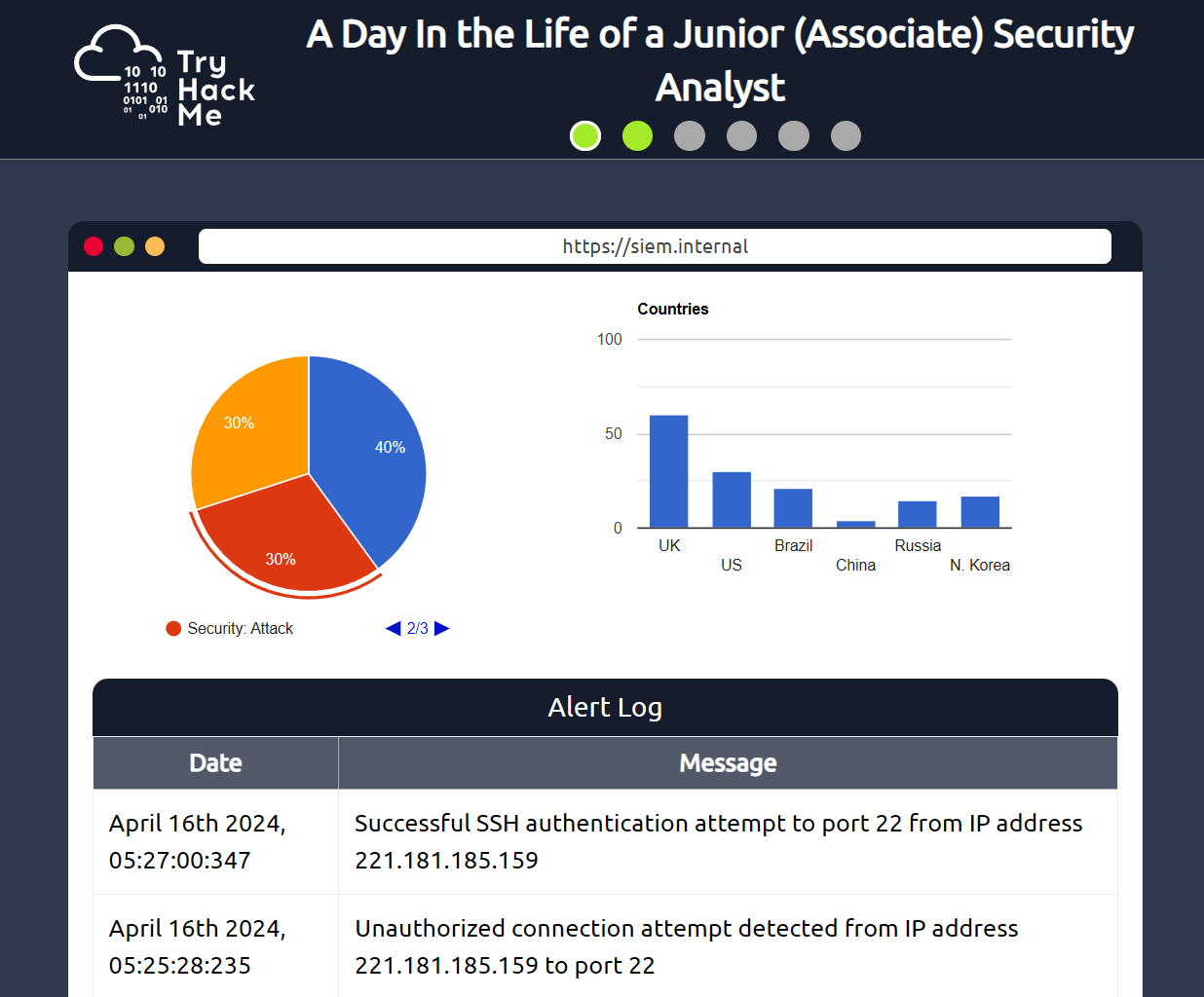

And the questions + answers:
Next up is the Pyramid of Pain - this is essentially a framework that demonstrates how certain IoCs are more troubling to a threat actor than another, and is used to enhance Cyber Threat Intelligence (CTI) in many cybersecurity solutions. From AttackIQ: "The Pyramid of Pain ... provides an ascending priority list of indicators against which security controls should be applied." So, starting from the bottom and working up:
Hash values are exceptionally easy for a threat actor to circumvent, as modifying a file by even a single bit and then recompiling will produce a different hash and therefore entirely sidestep an attempted control at this level. See below for given example:

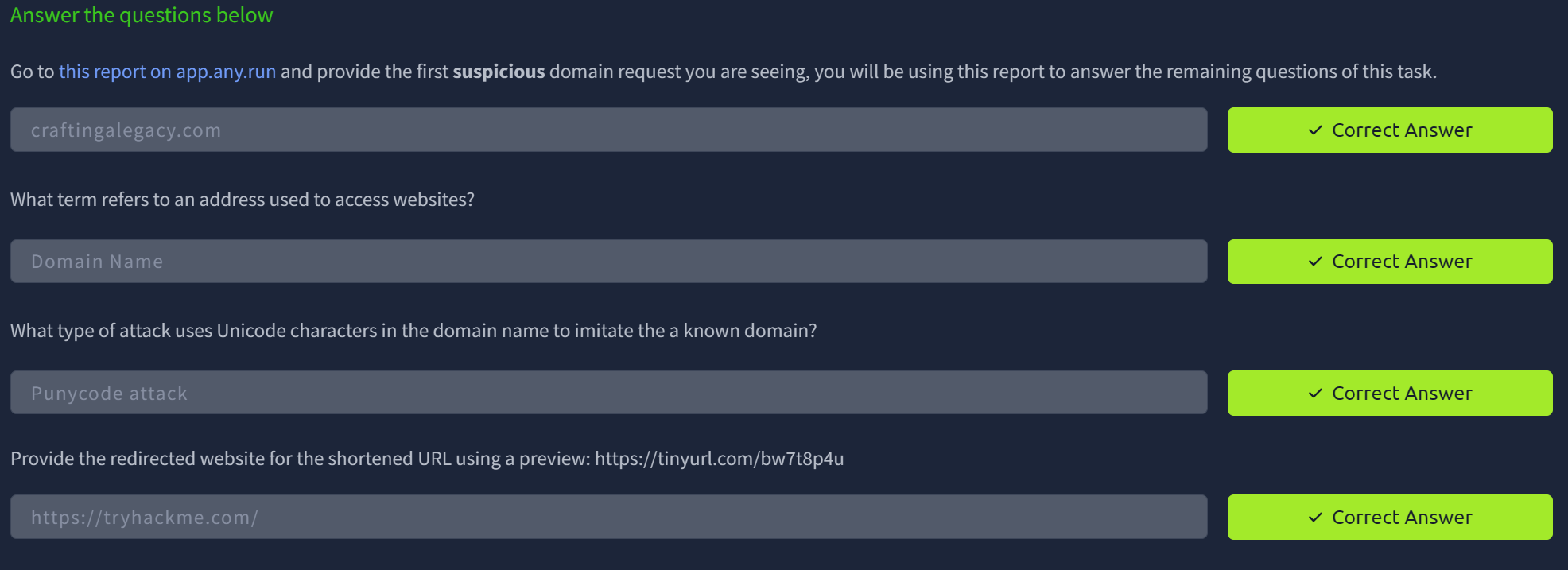
IP addresses are also quite easy for even less experienced adversaries to work around. Blocking or denying inbound traffic/requests from a given IP is not a bulletproof defense, despite being a common (and still useful) defense tactic. We are then given an example of how threat actors can work around a control at this level, and provided static reports from any.run to analyze and then answer the following:

Moving up the Pyramid once again, we have domain names. Direct from THM: "Domain Names can be a little more of a pain for the attacker to change as they would most likely need to purchase the domain, register it and modify DNS records. Unfortunately for defenders, many DNS providers have loose standards and provide APIs to make it even easier for the attacker to change the domain."
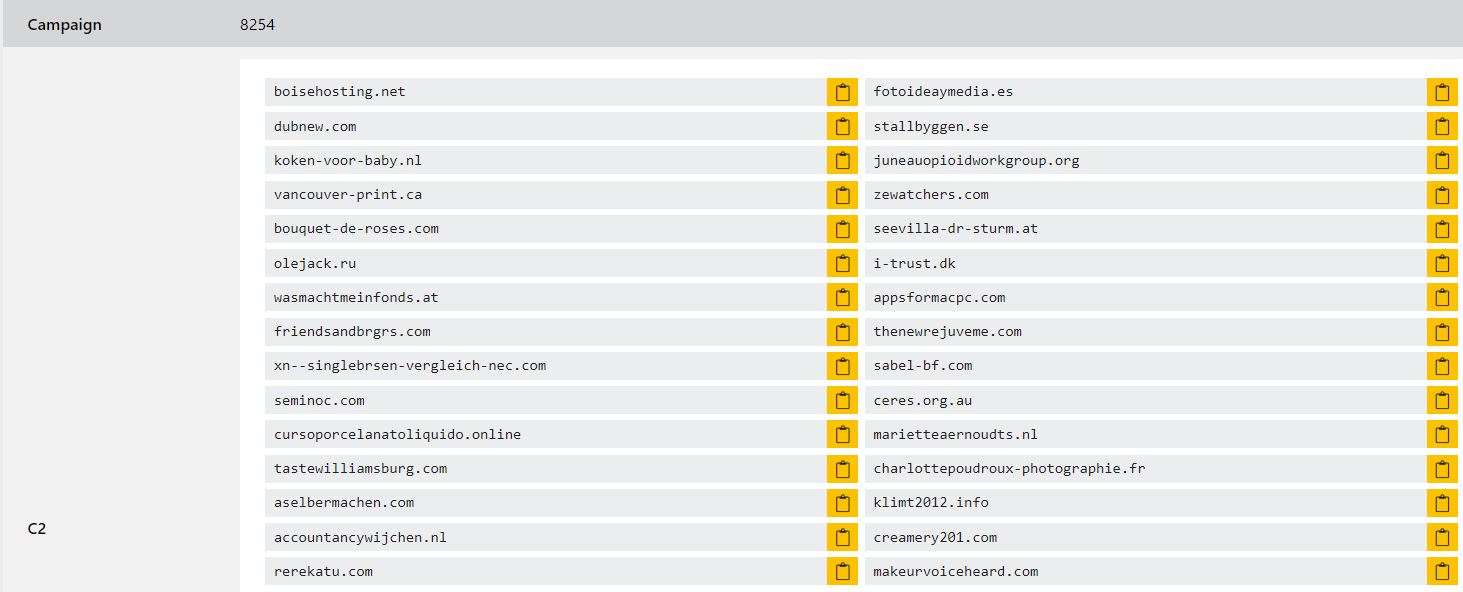
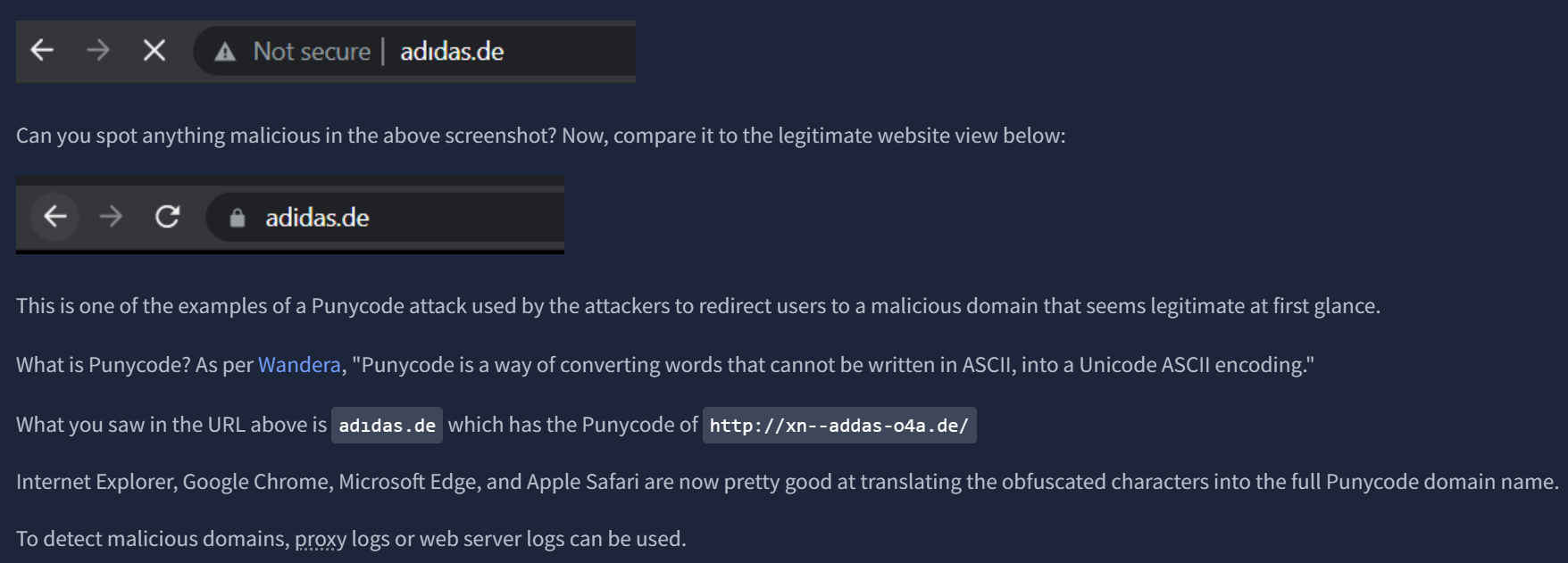
The module goes on to explain the use of URL shorteners, and how they are commonly used to hide malicious domain names, and provides a potential negation tactic in appending a '+' to the shortened URL to see the full domain you are being directed to. For example, "http://bit.ly/275hf9+” would show the actual destination of that link. Next, we circle back to the ever-so-useful any.run. Being a sandboxing service that executes a sample, it allows us to review connections such as HTTP or DNS requests, or see any processes attempting to communicate with an external IP.
Finally, we're given an actual sandboxed file on AnyRun, and asked to answer the following questions by analyzing the information in the pictured report:

Moving up another step into the 'yellow zone', we have host artifacts. This is where the attacker will begin to feel much more frustrated if the attack is detected as it would likely require them to change their tools and methodologies, which can be very time consuming.
From THM: "Host artifacts are the traces or observables that attackers leave on the system, such as registry values, suspicious process execution[s], attack patterns or IOCs (Indicators of Compromise), files dropped by malicious applications, or anything exclusive to the current threat."
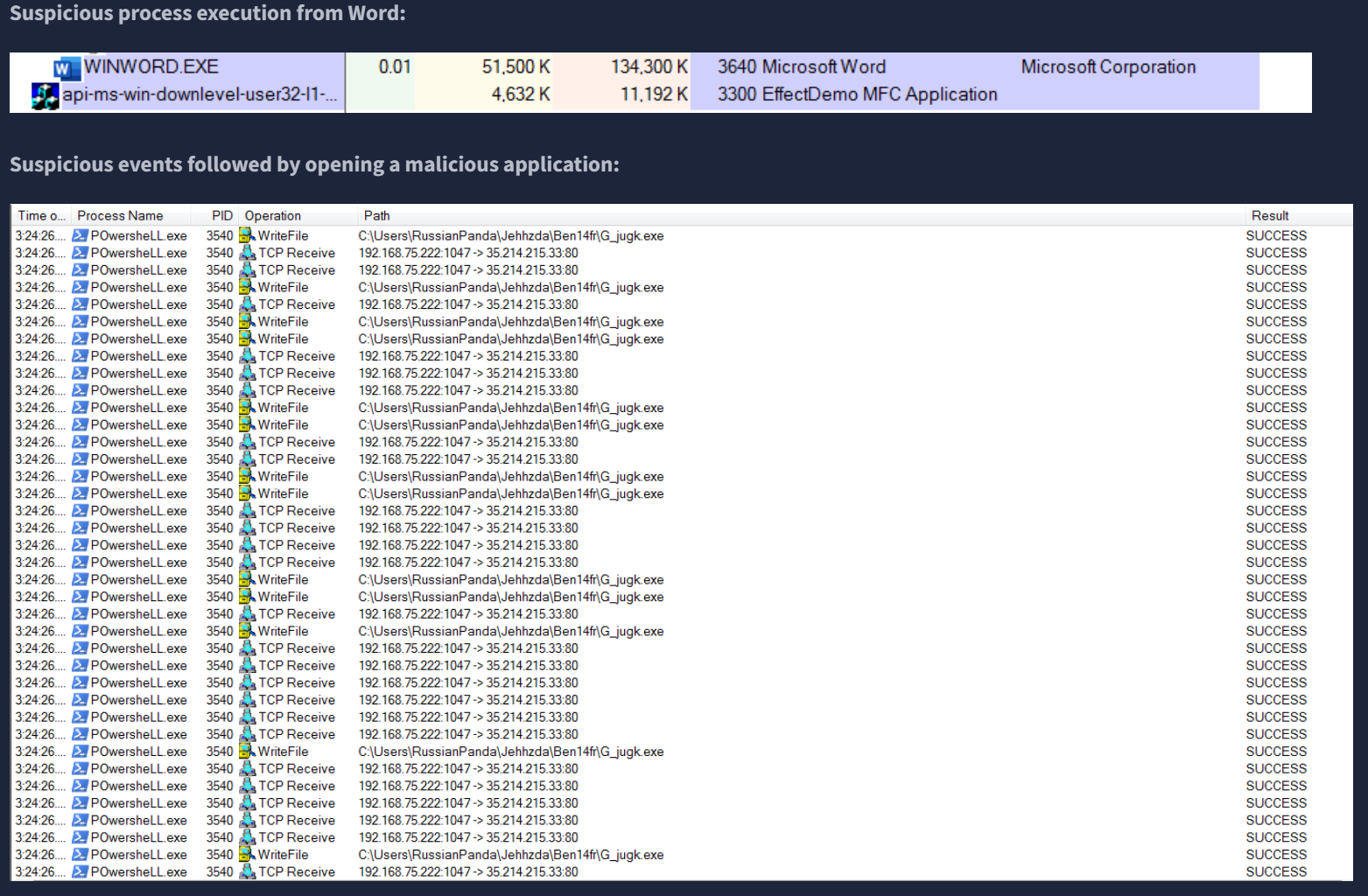
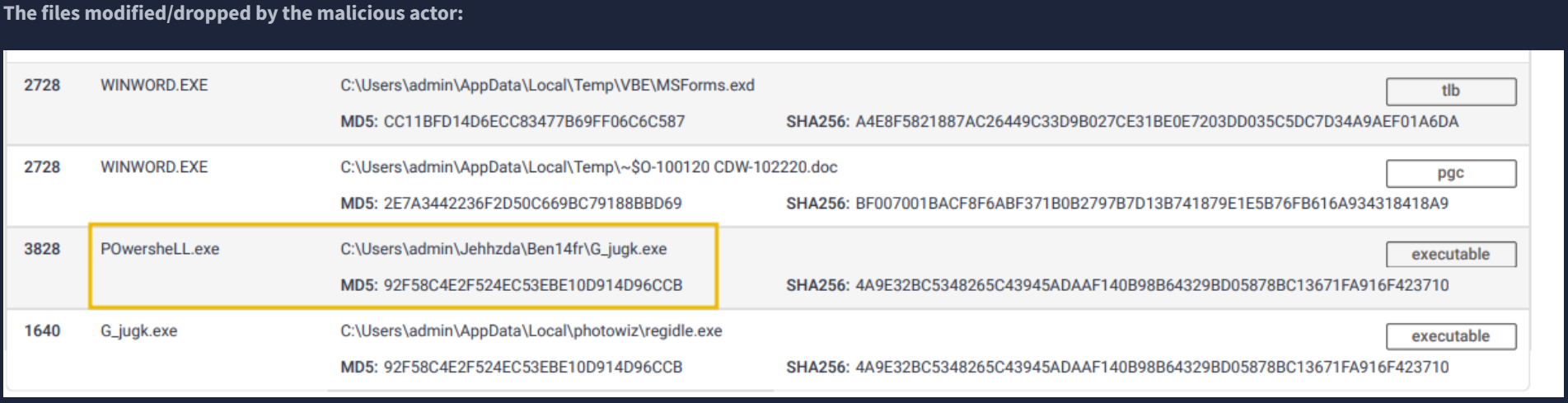
We are then given an example malware analysis report, and asked to answer several questions based on the information within it:

In the same 'yellow zone' as Host Artifacts are Network Artifacts. Again from THM: "A network artifact can be a user-agent string, C2 information, or URI patterns followed by the HTTP POST requests. An attacker might use a User-Agent string that hasn’t been observed in your environment before or seems out of the ordinary. The User-Agent is defined by RFC2616 as the request-header field that contains the information about the user agent originating the request."
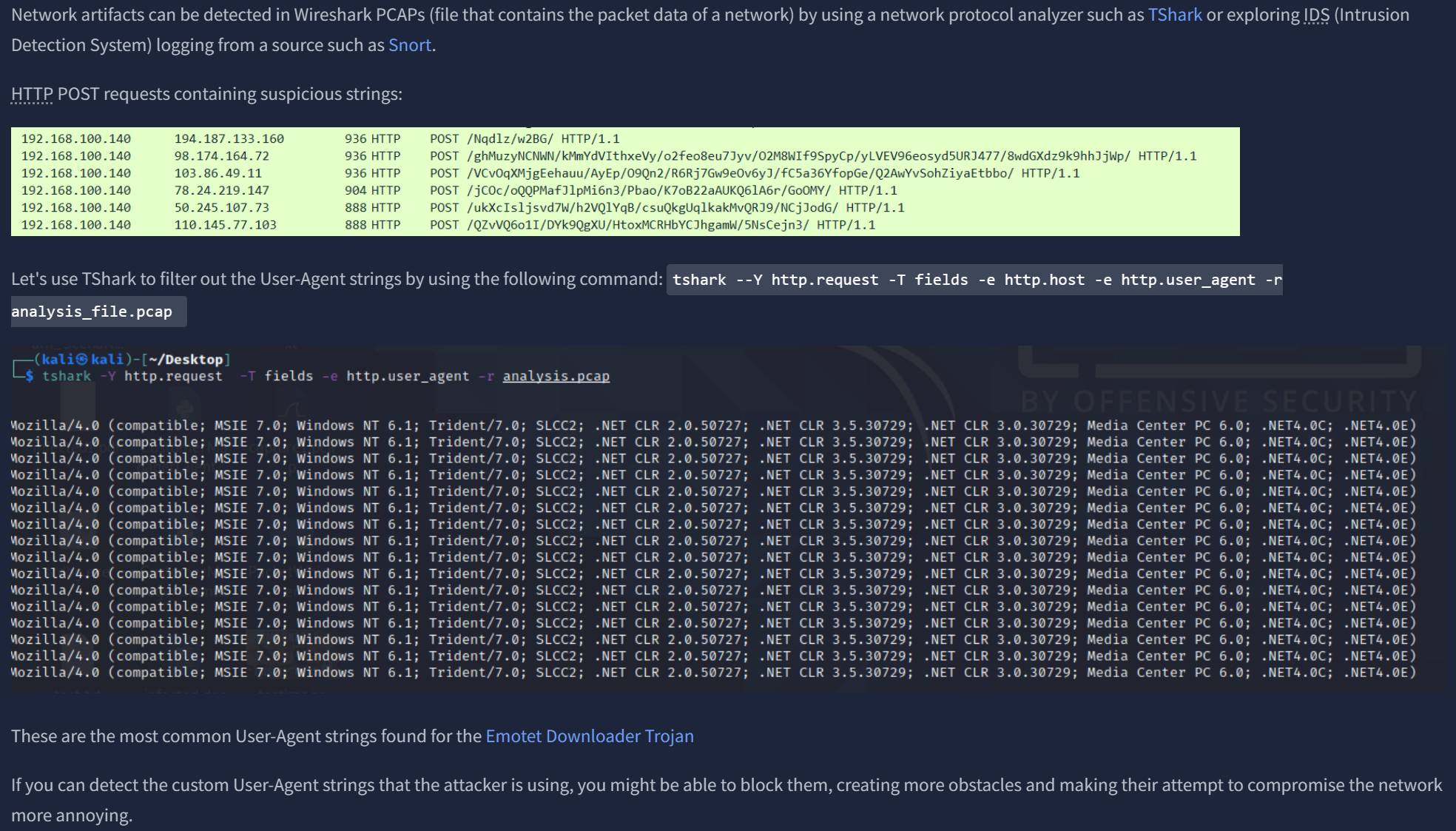
Then some questions regarding the above screenshots:

At this point in the Pyramid, an attacker will likely give up, or if they're sufficiently advanced and/or committed, will at least have to go back to the drawing board and create a new tool that serves the same purpose. Threat actors without sufficient resources to continue will often be deflected at this point.
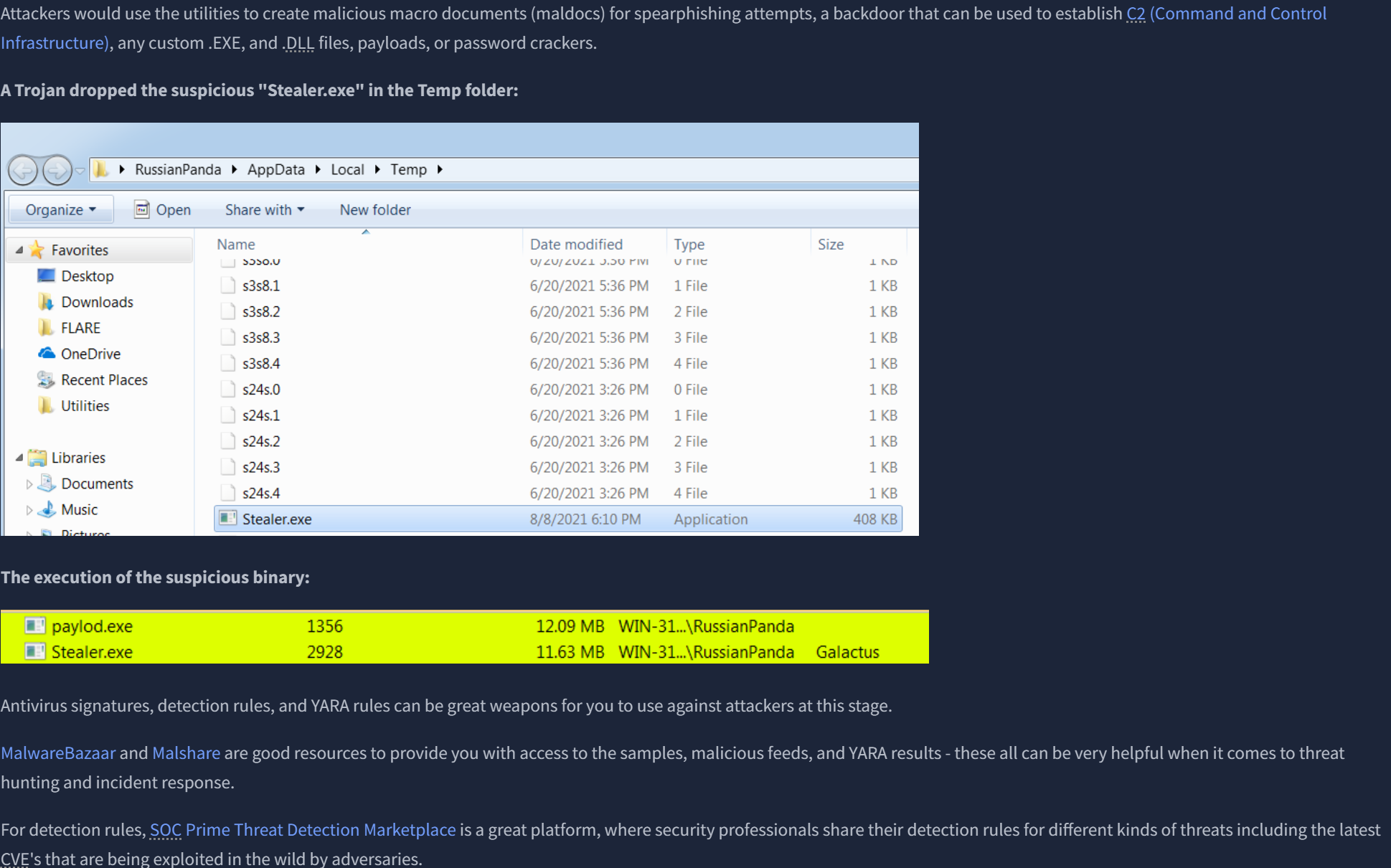
We finally reach the apex of the Pyramid of Pain, where we have Tactics, Techniques & Procedures. We get our first mention of the omnipresent MITRE ATT&CK Matrix, which is a framework that lists, essentially, all the steps taken by a cyber adversary to achieve their goal in almost any possible circumstance. By detecting and responding to TTPs quickly, we leave the threat actor almost no chance to fight back.
The practical involves matching descriptions to each 'block' of the Pyramid, then entering the flag awarded for doing so.
We finished the module!
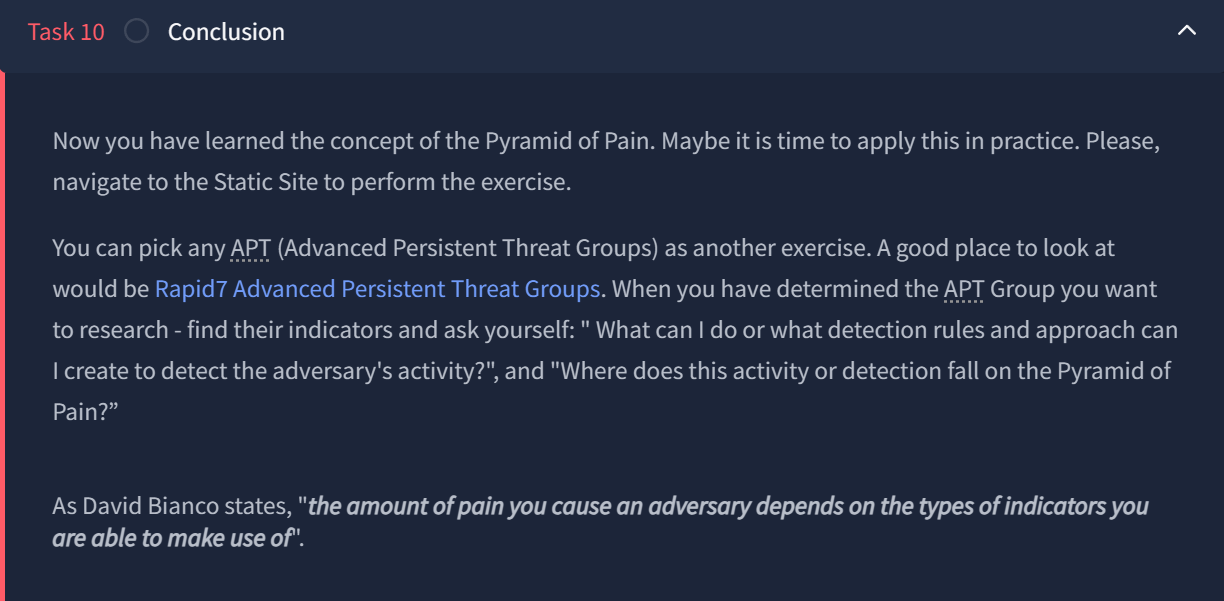

Moving on to the next module - Cyber Kill Chain! In the words of THM:
The term kill chain is a military concept related to the structure of an attack. It consists of target identification, decision and order to attack the target, and finally the target destruction.
Thanks to Lockheed Martin, a global security and aerospace company, that established the Cyber Kill Chain® framework for the cybersecurity industry in 2011 based on the military concept. The framework defines the steps used by adversaries or malicious actors in cyberspace. To succeed, an adversary needs to go through all phases of the Kill Chain. We will go through the attack phases and help you better understand adversaries and their techniques used in the attack to defend yourself.
Attack Phases:
The topic of OSINT is introduced, and specifically email harvesting is focused on with tools like theHarvester.
After successful recon, the threat actor combines malware and exploit(s) into a deliverable payload.
Delivery is the method of distributing the payload: phishing emails, USB drops, watering hole attacks, etc.
The attacker exploits the vulnerability. OWASP Top 10 is introduced. Zero-days are also mentioned.
Persistence via web shells, backdoors, modified services, registry keys, or [Timestomping].
Beaconing using HTTP/HTTPS, DNS tunneling, or other channels.
Once inside, the attacker might:
Match general concepts to the stages of the CKC.
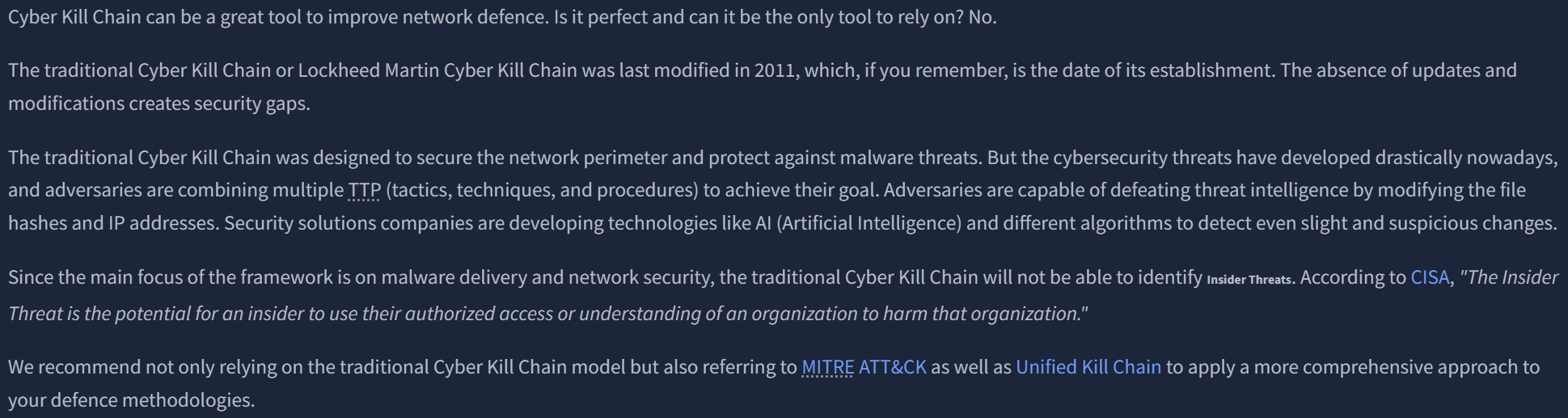
THM introduces a more modern and detailed model, used in complement to others.
STRIDE, DREAD, CVSS frameworks and concepts of identifying risk are discussed.

Another round of matching TTPs to their respective phase.

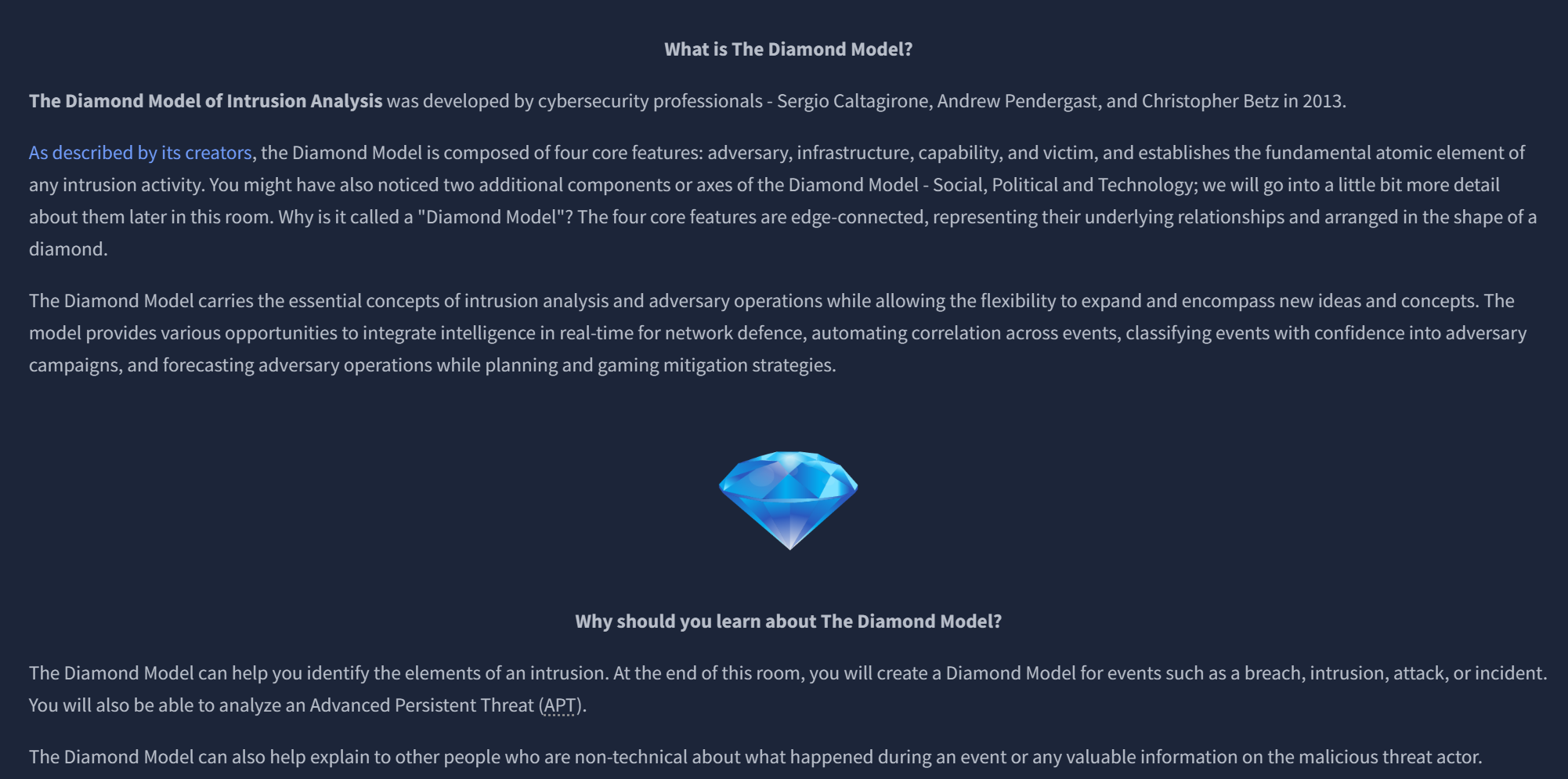
After several short review sections and questions, we create our own Diamond Model based on the 2016 Ukrainian Power Grid Attack.
Intro to ATT&CK, CAR, Engage, D3FEND, CVEs, and more.
"MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations." Started as FMX, now includes Windows, Linux, macOS, and supports Red and Blue team efforts.

Deep analytics for detections beyond the ATT&CK technique level.
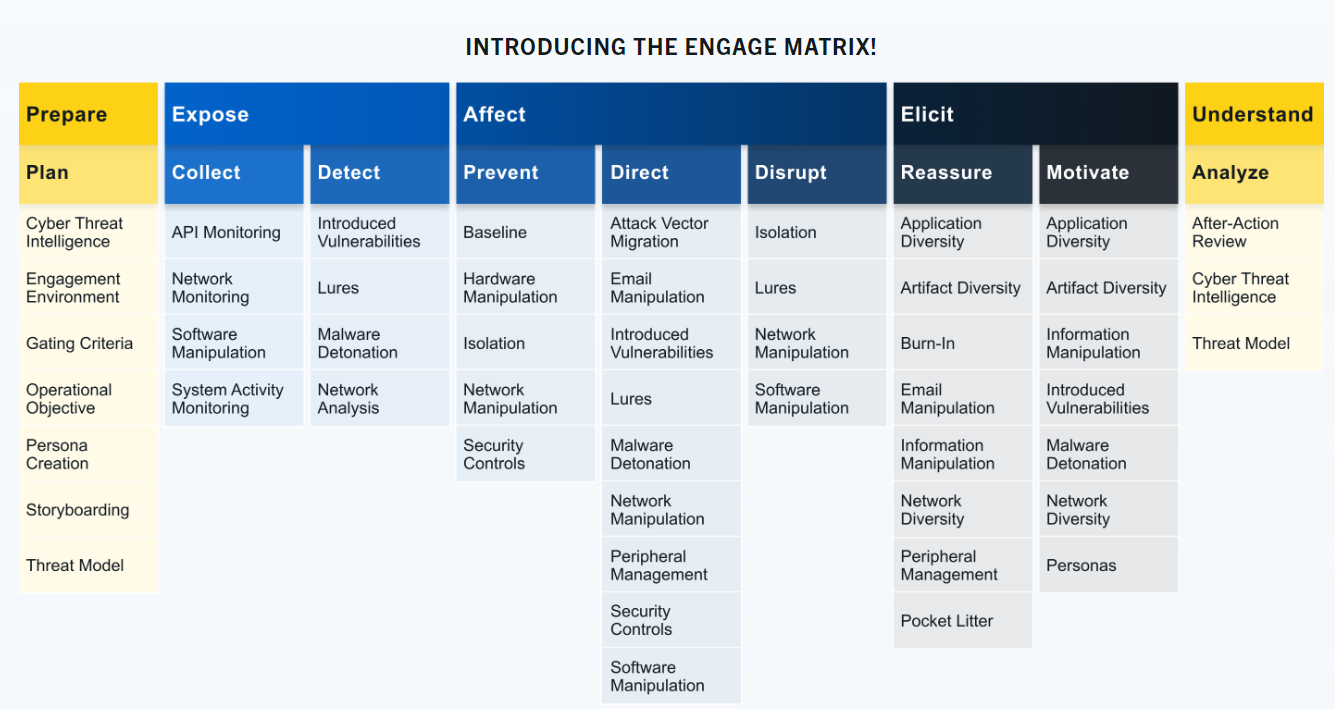
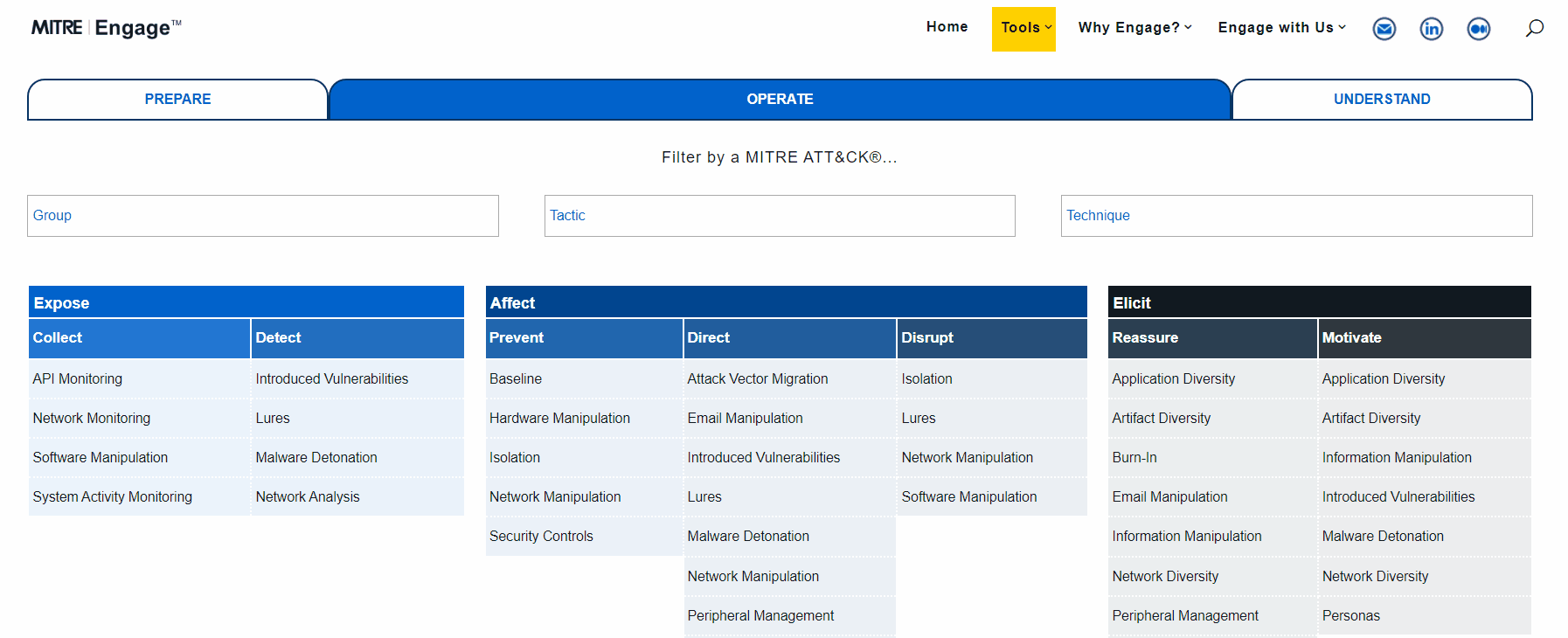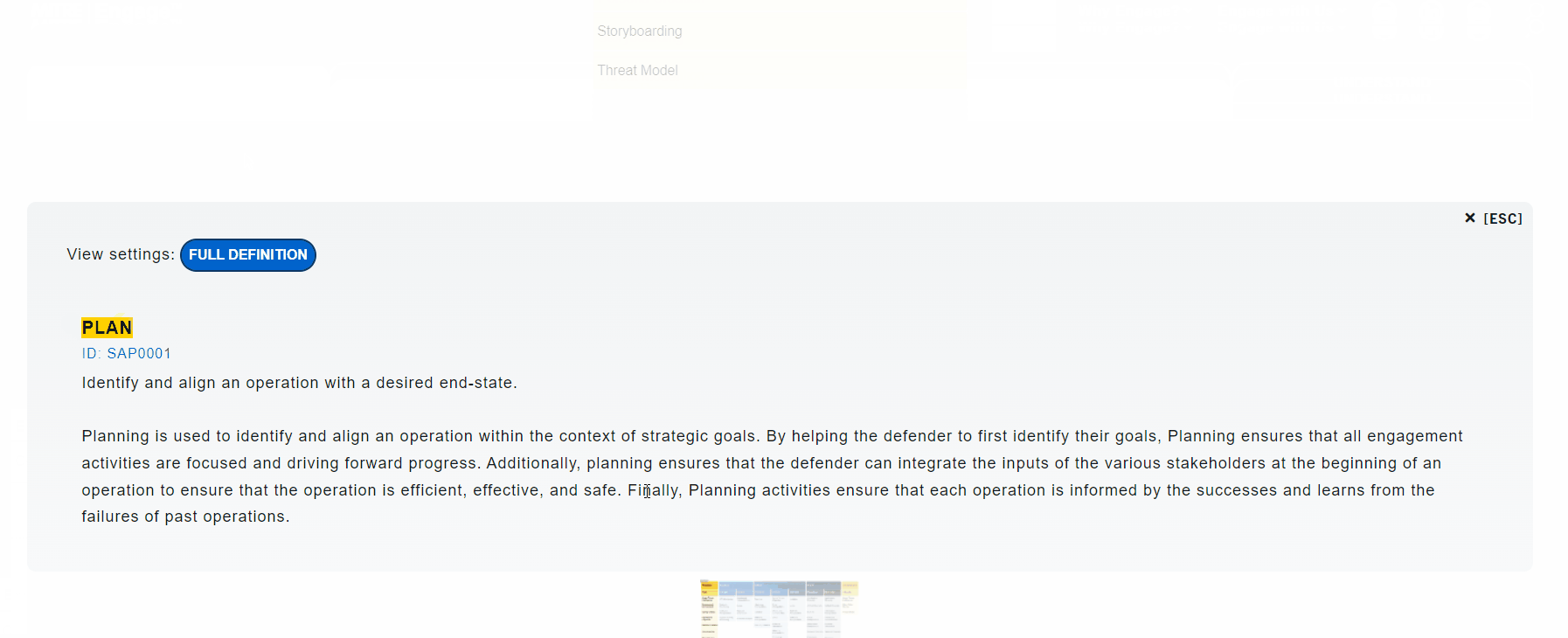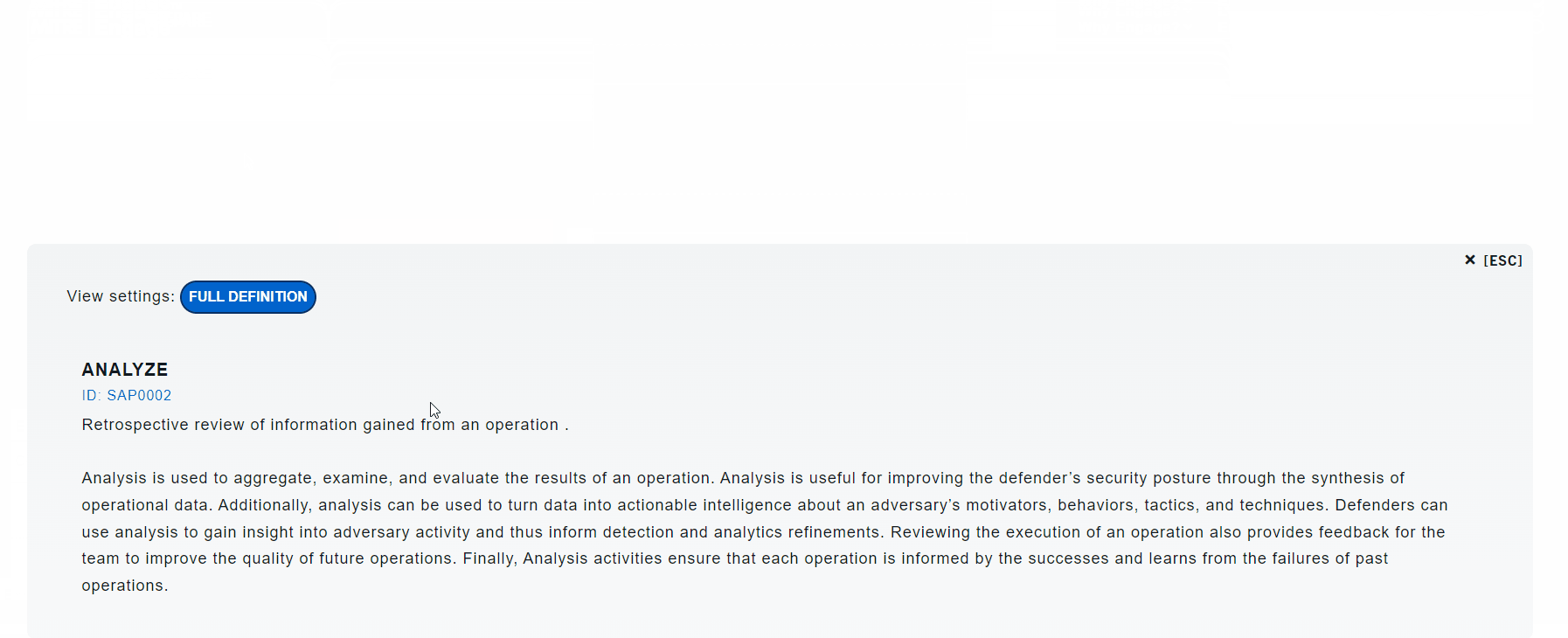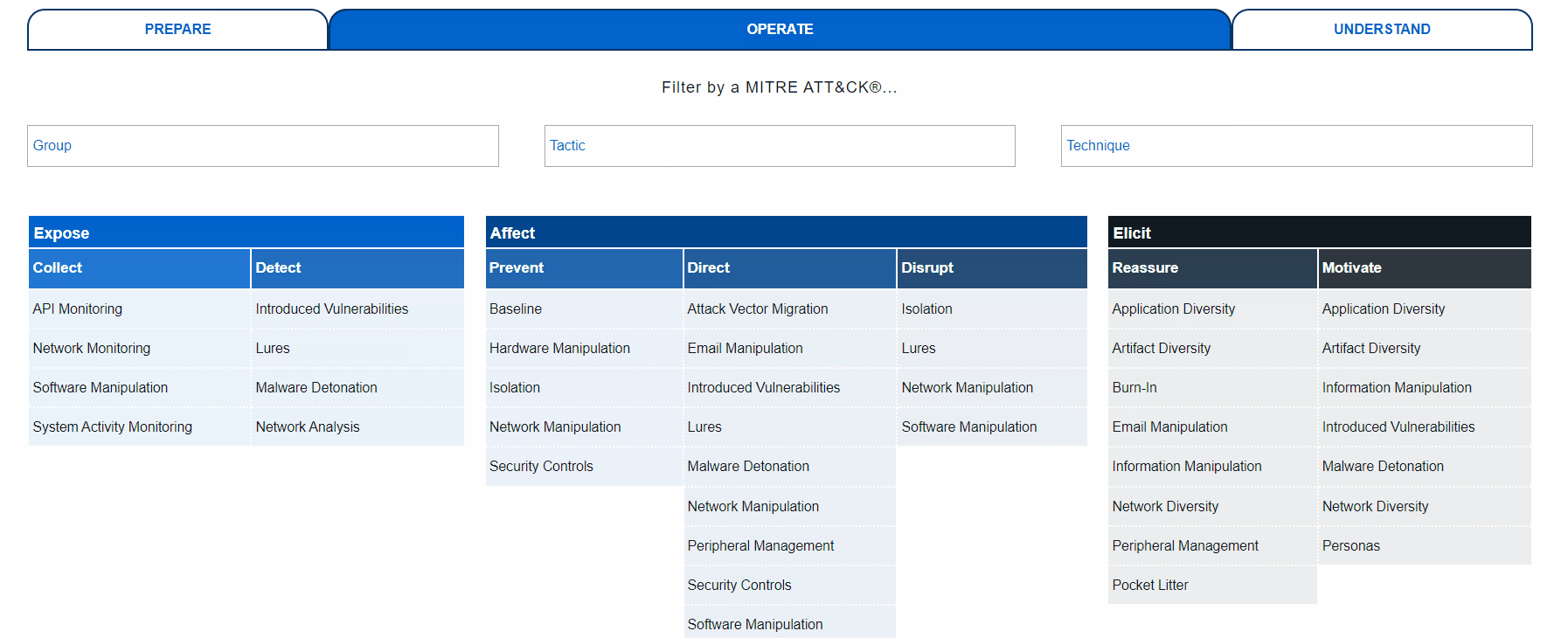
Operational activities include: