Azure VM with Sentinel – Personal SIEM / Home SOC
After some hands-on work through various learning paths, virtual internships and to satisfy my own insatiable curiosity, I built out my own test SIEM with a custom rule, set to detect successful logins via RDP (which was intentionally left open for testing purposes). Thanks to the free $200 credit for new Azure accounts, this project even worked out to be the best kind of cheap... Free!
Creating the VM
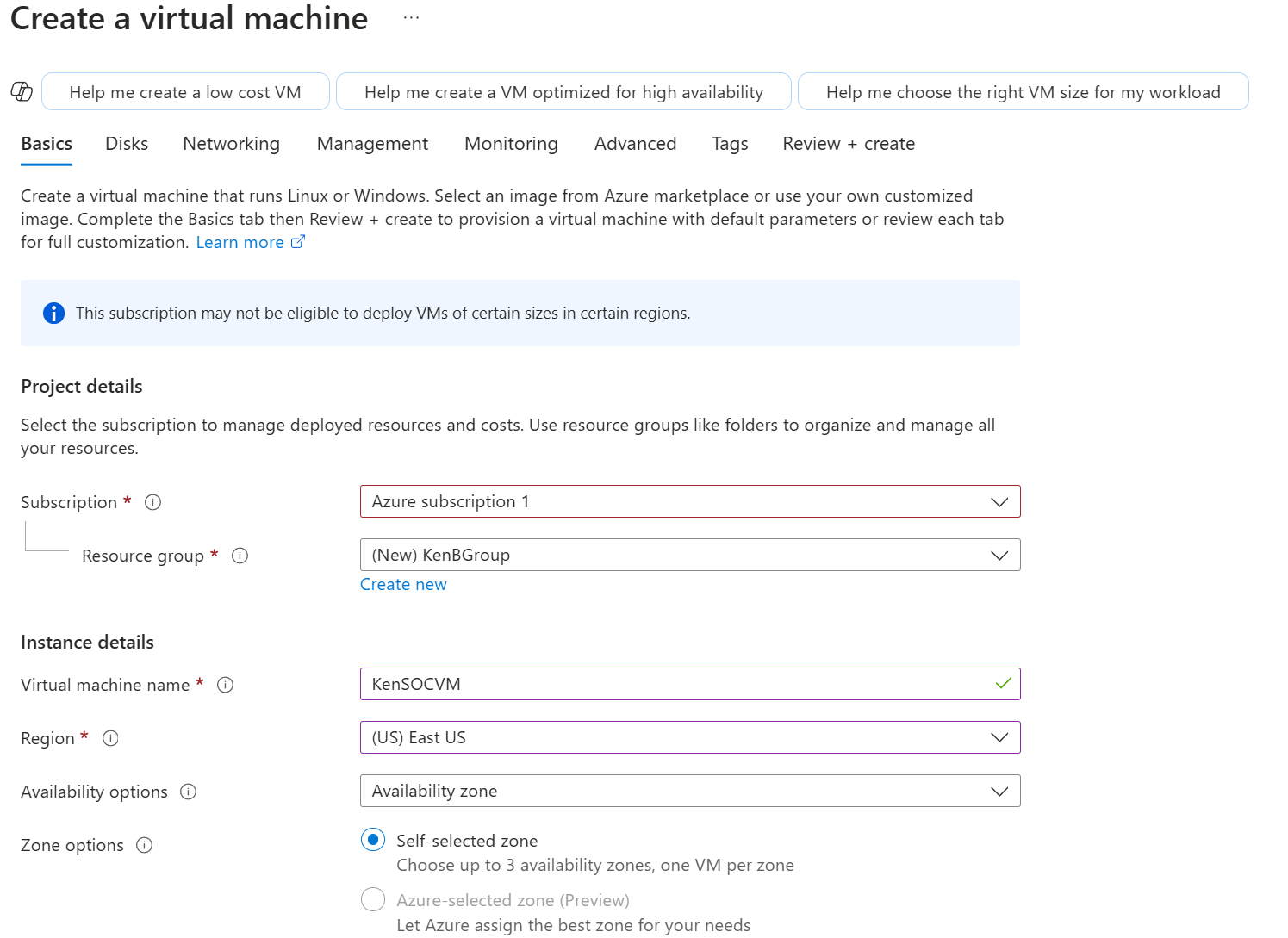
The first step after getting started on Azure was, of course, to create a relatively simple Windows 10 Pro VM...
Sentinel / Log Analytics Workspace Setup
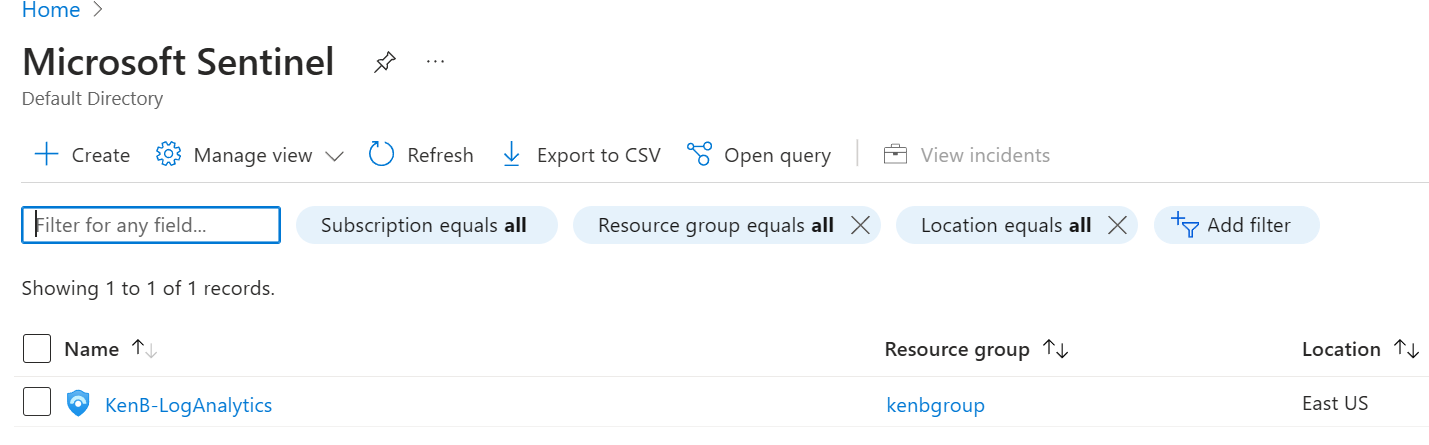
Next up was setting up Sentinel itself. I continued with my apt naming trend.
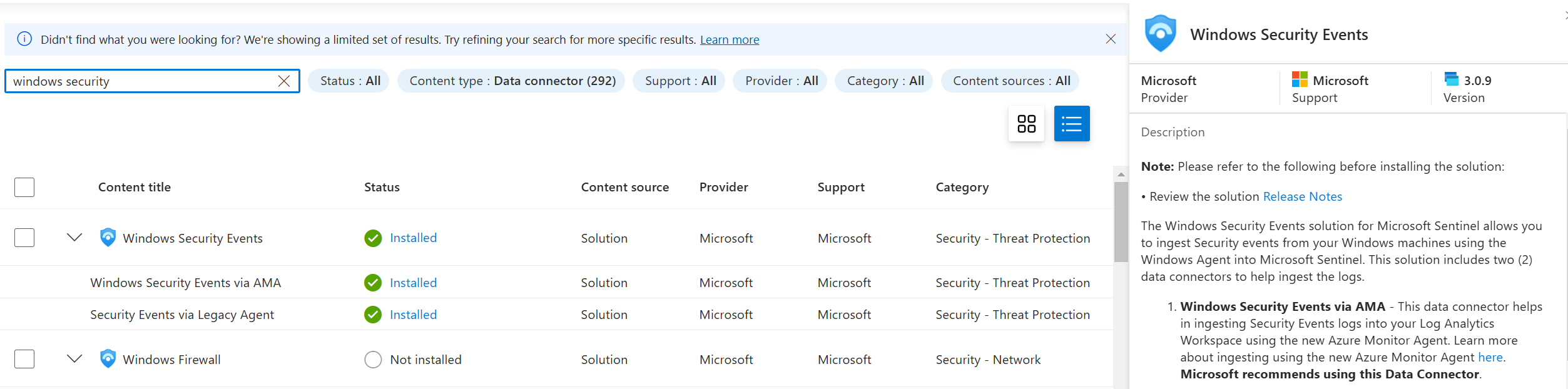
After this, I installed the Windows Security Events Data Connector via the Content Hub...
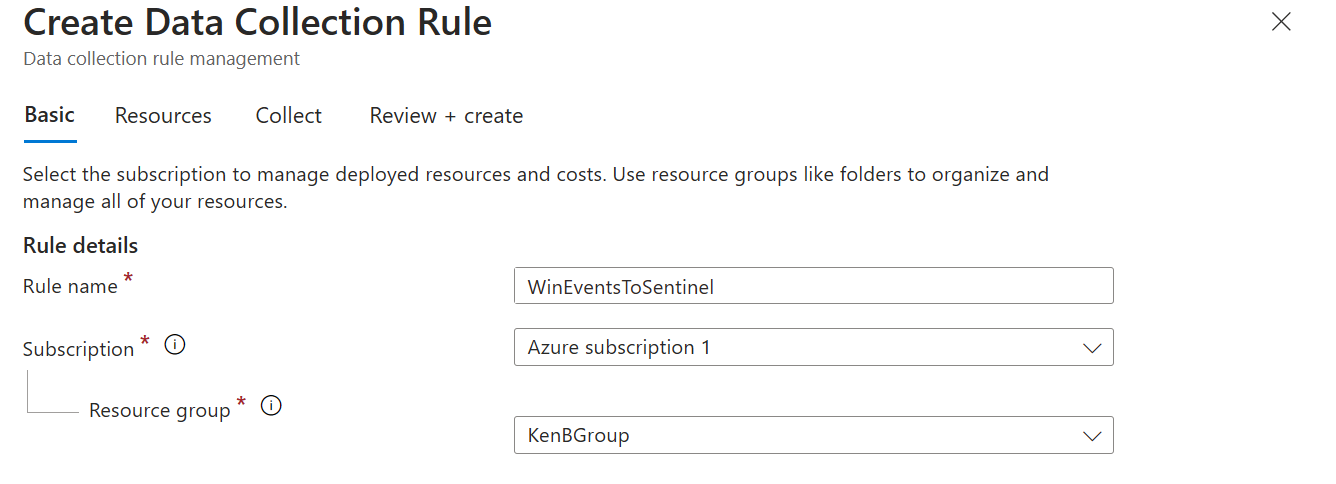

Now that we’re receiving logs from our VM, we want to create a useful detection rule...
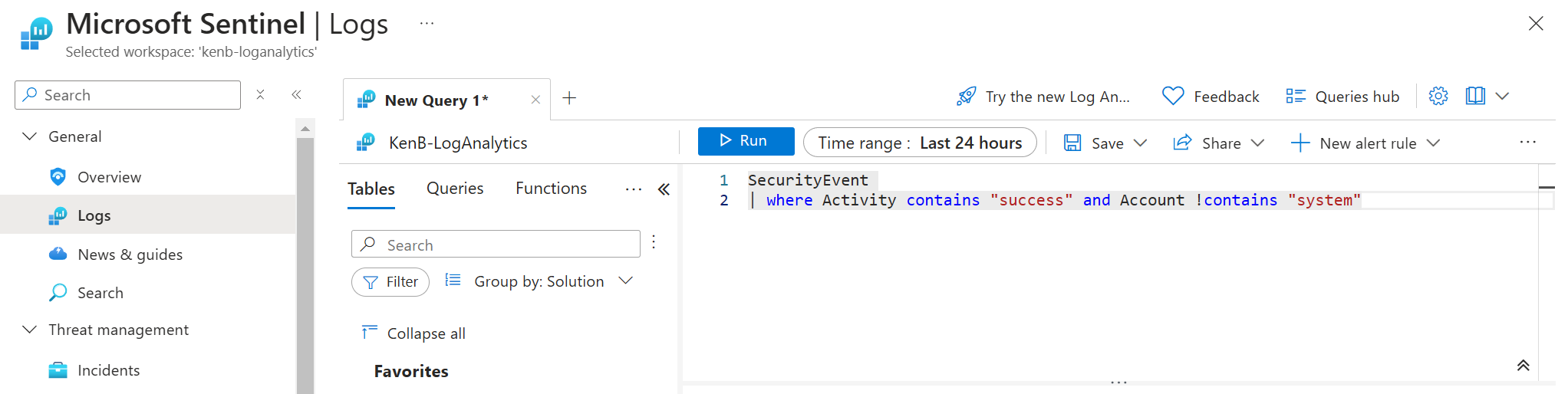
We categorize it under TA0001 - Initial Access.
Testing it Out
I RDP into the VM and sign in with the previously created administrator credentials...
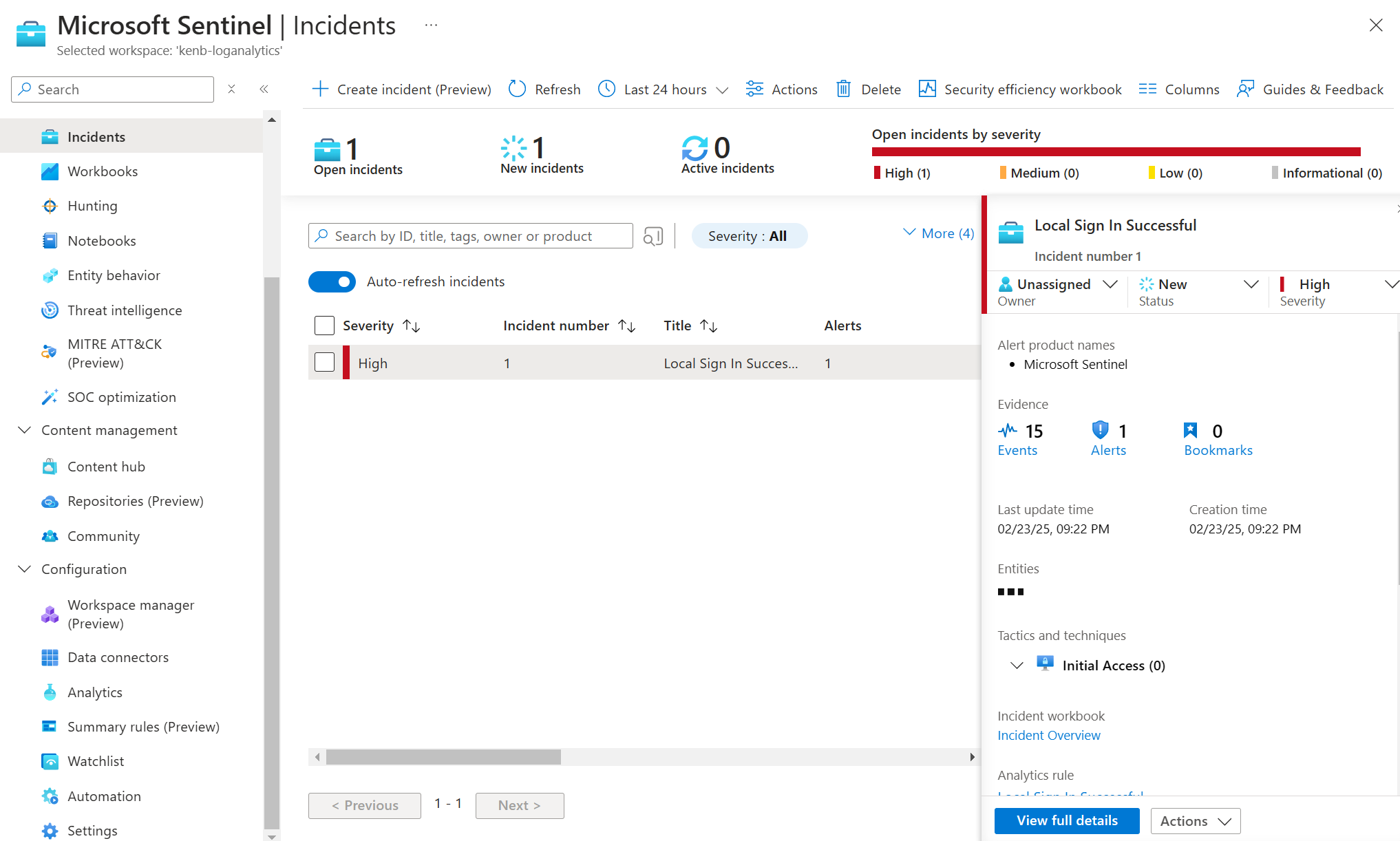
A quick switch from 'Allow' to 'Deny' in the port rules should do the trick.
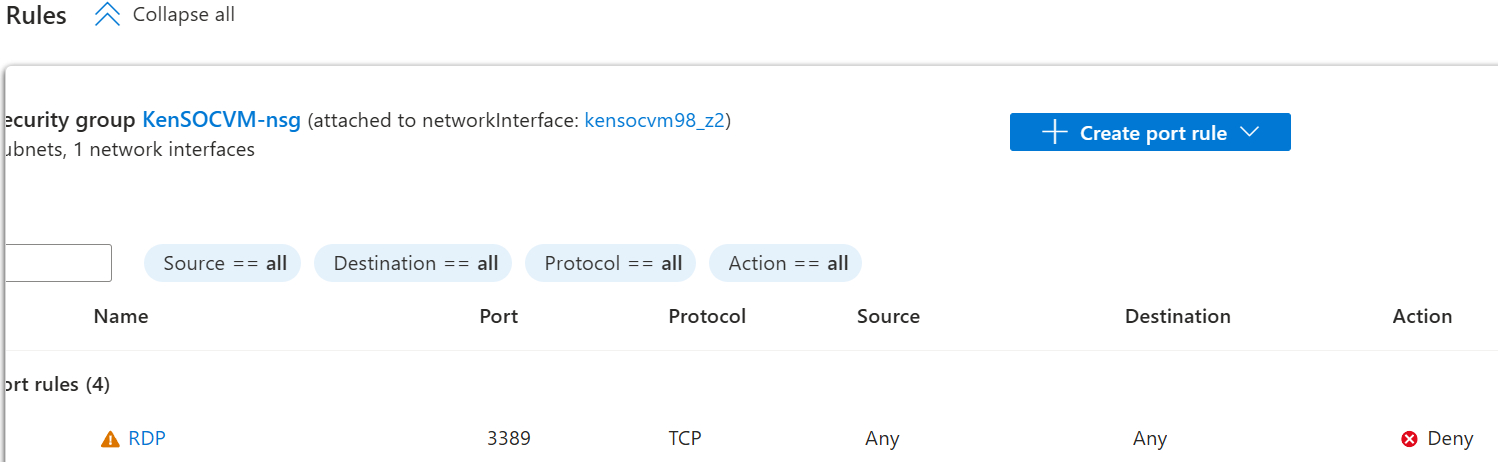
With that, we wrap up this basic but very useful experiment! This is just the tip of the iceberg, and I'll definitely be back to do more with this setup in the future. Thanks for reading!